Enterprise software supply chain management
ACCELERATING INNOVATION FOR 15+ YEARS
$31M
80%
503%
95%
Superior data is our lifeblood
Alternative tools are prone to false positives and negatives because they scan apps “as declared” and trust developers to disclose the truth about dependencies embedded in software.
Sonatype scans apps “as deployed” utilizing Advanced Binary Fingerprinting (ABF) to reflect the truth about third party risk.
Security that never sleeps
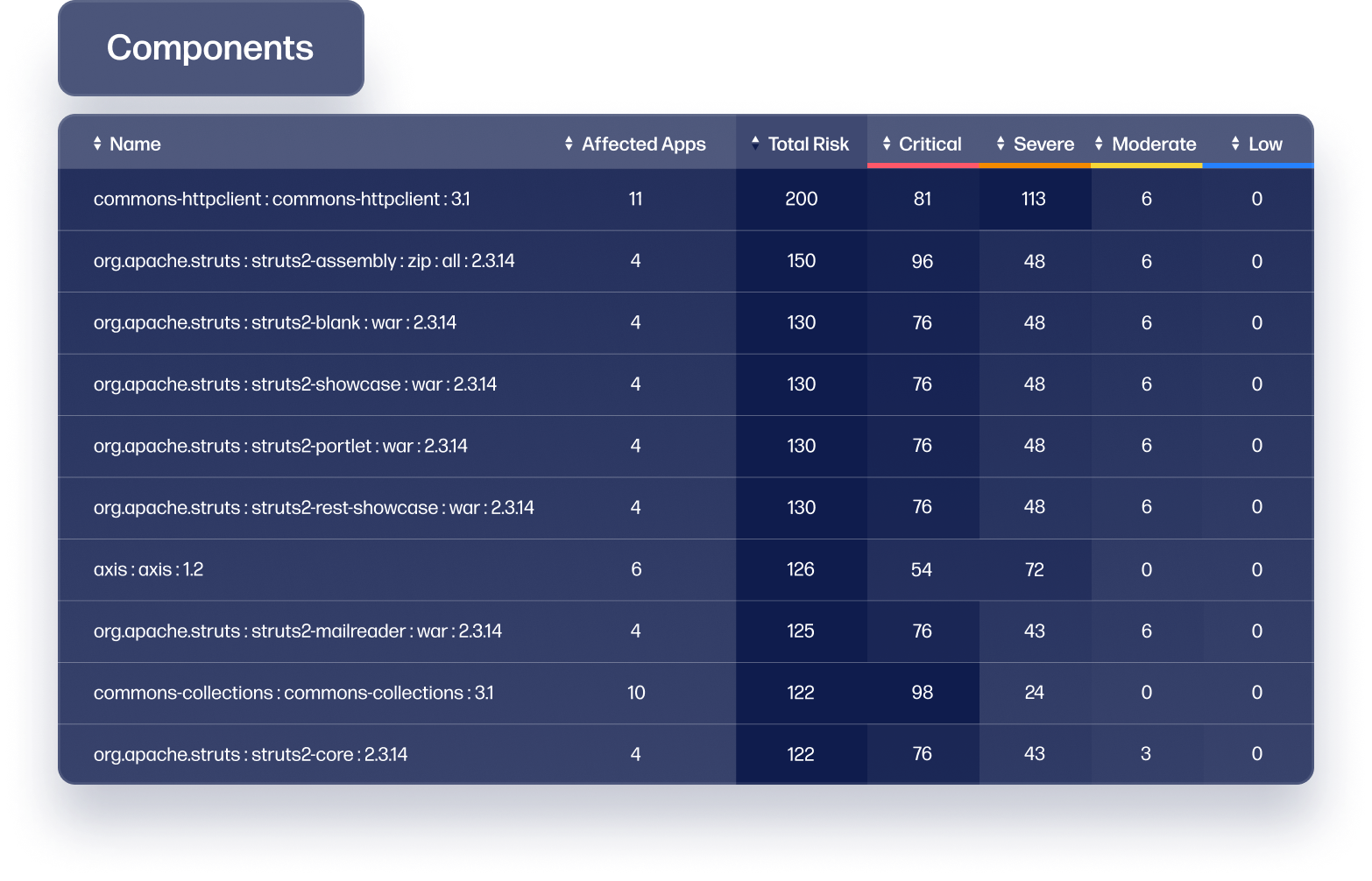
Unite teams within mission control
For developers
For application security
For legal & compliance
Enforce policies automatically
Run products anywhere
Cloud
Self Hosted
Disconnected
Access enterprise support
Workshops & services
Start strong with training in a public classroom, at your site, or online. Sonatype can also provide custom training courses for your specific needs.
Self-service training
Get help from online learning modules, technical guides, and videos directly from within Sonatype’s detailed product documentation.
Dedicated coaching
Work with a proactive Customer Success team member to outline a strategy and set up your platform to achieve your desired outcomes.
Online community
Access and contribute to community plugins in our online community. Engage in forum discussions, office hours, and share ideas with fellow innovators.
-
“We are very happy with the Sonatype support. We have occasionally had issues to handle and the Sonatype support team answers our questions in minutes. This is VERY important for us.”
Emre ErkekDevOps Engineer, Kredi Kayit Burosu -
“The training was very thorough, and the teacher was knowledgeable enough to respond to many questions from the team. The workshop raised many questions that our company was not aware that we needed to address.”
DevOps Engineer, Equifax
Insights for innovators

8th Annual State of the Software Supply Chain

Software Supply Chain Management: An Introduction