This week, PyPI and NuGet open source repositories have been flooded with more than a hundred spam "Roblox" packages pointing to bogus links. Additionally, npm, the largest NodeJS package registry has also been seen battling spam packages.
In each case, the packages are practically empty; with no functional code. But, their README pages link to spam domains offering "free Robux generators" and tools for creating in-game items like custom skins.
Spammers polluting open source registries with links to pirated movies and warez sites is not novel — such shenanigans may help boost SEO for spam domains. This particular spam campaign tracked by Sonatype, along with our most recent discovery of malicious Roblox cookie and Discord token stealers paints an interesting pattern.
PyPI, npm, NuGet Polluted With "Robux" and Fortnite Spam
Yesterday, my colleague and data scientist Cody Nash alerted us to funny-sounding PyPI packages flagged by our automated malware detection systems. Except, these packages were neither malicious nor dependency confusion PoCs, and contained no functional code.
All of these packages and their READMEs pointed to a spammy domain: freerobux[.]best.
PyPI removes more spam packages named after Roblox' Robux. These contain no functional code but link to bogus domains like:
— Ax Sharma (@Ax_Sharma) February 14, 2022
🌐 freerobux[.]best
Reported by @Sonatype @CodyZNash
#opensource pic.twitter.com/ysXu6IagHo
After our report to PyPI, these four dozen-plus packages were taken down. But, in the last 24 hours threat actors seem to also have targeted NuGet, the open source registry of .NET packages with Robux spam [1, 2]:
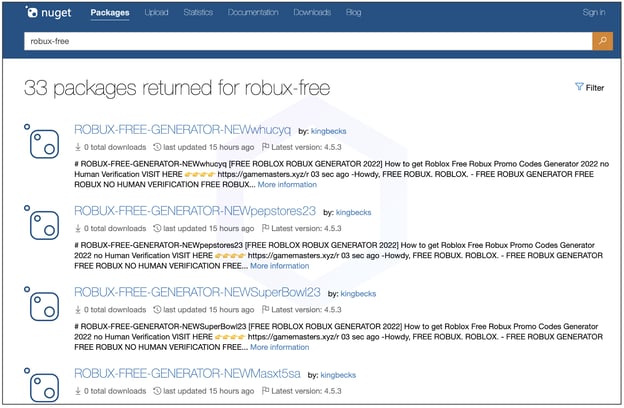
In addition to the same freerobux[.]best domain seen on NuGet, other domains used for the spam campaign include:
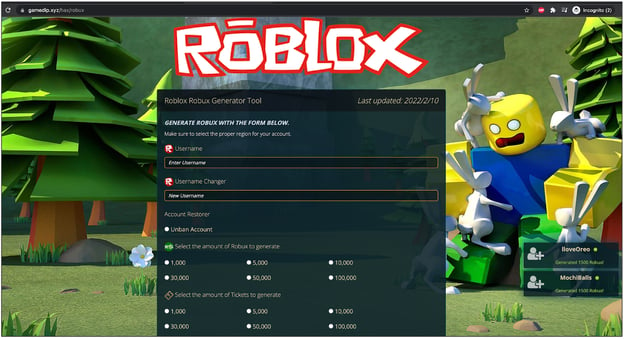
- gamedip[.]xyz
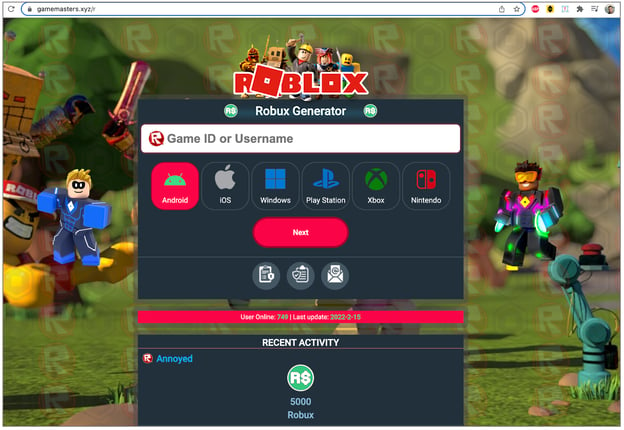
- gamemasters[.]xyz
All such links lead to bogus "Robux Generator" pages, as shown below:
Domain gamedip[.]xyz with Roblox and Fortnite spam:
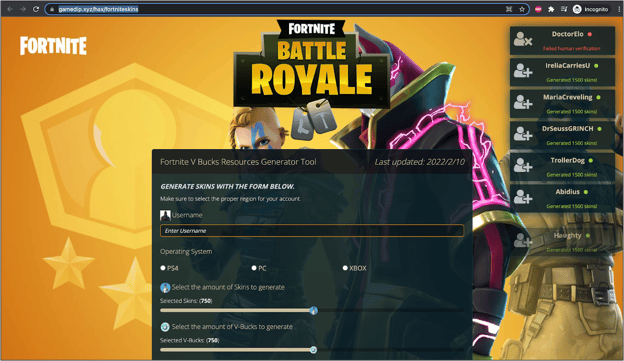
Another aspect of this campaign targets Fortnite players by leading them to so-called "skin generator" tools:
And the JavaScript open-source ecosystem, npm, is no alien to such spam campaigns. Despite removing plenty of such packages this month, npm, still seems to have a few more to tackle — 25 seen at the time of writing.
 Image: More Roblox/Robux spam packages emerge (left) after npm removes some (right)
Image: More Roblox/Robux spam packages emerge (left) after npm removes some (right)
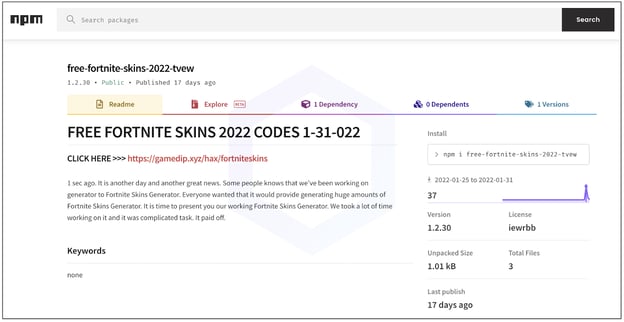
In addition to PyPI, Sonatype also reported these findings to npm and NuGet maintainers.
Why Are Open Source Attackers Targeting Gamers and Leveraging Gaming Platforms?
Attackers infiltrating open source repositories for targeted supply chain attacks is a clear-cut use case. We've seen this in the event of malware posted to software registries, as well as legitimate libraries like 'coa' and 'rc' getting hijacked to deploy crypto miners and password-stealers.
But, what explains the attackers' odd infatuation with Discord, Roblox, and gaming platforms? Is this all a red-herring or part of a bigger malware distribution strategy?
It started around September 2020, when an npm package 'fallguys' was found, disguising itself as an API for the popular video game Fall Guys: Ultimate Knockout. Its actual purpose, however, was to read your web browser's 'leveldb' files and exfiltrate sensitive tokens via a Discord webhook.
Weeks after this development, Sonatype discovered a successor to this package, with extended capabilities. The 'discord.dll' npm package and a series of identical typosquats were counterfeit components aimed at Discord users and developers.
Discord is a heavily used IM app with widespread usage among gamers. Although the platform has repeatedly been abused by nefarious actors who host malware [1, 2] and malicious "webhooks."
By late 2020, tracking this rampant Discord malware campaign by Sonatype eventually led us to discover an all-new 'CursedGrabber' malware family employed in these attacks.
And in November 2021, nearly a year later, we tracked the Noblox.js npm malware campaign aimed at Roblox and Discord developers, which marked the first documented case of ransomware code being distributed through an open source registry.
In a subsequent report, the maintainer of the official Noblox.js package (a Roblox API wrapper) claimed a particular attacker was persistently abusing his "Noblox.js" brand to attack the wider user base with malware, and continued to publish newer variants to this end. And, further, the threat actor attested to the sentiment on our blog.
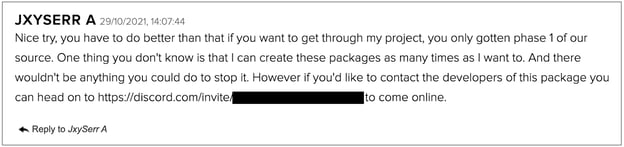
Even today, the Roblox and Discord trend is ongoing among OSS attackers. At the start of this month, we saw some npm packages stealing Roblox security cookies and Discord tokens. And the same week even more Discord token grabbers emerged on npm:
More #npm Discord token stealers. Analyzed by researcher @R44MB00 of @Sonatype
— Ax Sharma (@Ax_Sharma) February 10, 2022
discord-selfbot-tools
aployscript
discord.js-selfbot-aploy
discord.js-selfbot-aployed
discord.js-selfbot-aploys
discord.js-selfbot-aployscr
discord.js-selfbot-aployscript
discord.js-aployscript-v11 pic.twitter.com/97BNW9lLO4
The Love for Discord
Of note here is the fact that platforms like Discord may not be acting fast enough to thwart attackers or shut down malicious webhooks. In the course of our security research activities, we have frequently observed malicious "attachments" remaining available on Discord CDNs for weeks or more, even after reports of malware sprung up in news and among the wider community. Similarly, although open source registries may have taken down the malicious packages, their Discord webhooks remained online even days later. This delay in actively tackling threat actors and addressing malware reports encourages attackers to leverage Discord as a "stable" platform for hosting their malicious payload.
Roblox's Younger Audience
When it comes to Roblox, the platform has drawn controversy. Last year, People Make Games criticized Roblox for allegedly exploiting 9- to 15-year-olds by making heightened claims of earning "serious cash," from developing Roblox games, which doesn’t always end up being the case.
"On Roblox, many young devs crunch and burn out, they’re not privy to ongoing dev discussions about healthy working practices," shared a professional Roblox creator anonymously, according to an NME report.
The presence of relatively young users and novice developers on the Roblox platform may incentivize attackers to further dupe those who may not fully understand their way around. They may also fall for spam attacks like this, or the aforementioned Roblox/Discord counterfeit components laden with malware.
Low Barrier to Publish to Open Source
As I've said before, open source systems are open to everyone: that includes both folks looking to contribute to the community in good faith and adversaries. Publishing to registries like PyPI, npm, NuGet is quite easy for anyone. While the low barrier to entry makes open source an attractive platform for newcomers and regular contributors, without some security roadblocks, the entire ecosystem can become a cesspool of malicious attacks: from spam and phishing to cases of typosquatting malware, hijacked components, and dependency confusion infiltrating these registries.

Ax is a security researcher, malware analyst and journalist with a penchant for open source software. His works and expert analyses have frequently been featured by leading media outlets including the BBC. Ax's expertise lies in security vulnerability research, reverse engineering, and cybercrime ...
Explore All Posts by Ax SharmaTags
