Sonatype's focus on developers brings more insights into software dependencies, clearer policy exceptions, and support for PHP users. This Sonatype Platform update will help developers more easily remediate vulnerable open source usage across their projects.
New in Sonatype Lifecycle
Many organizations still operate with a scan-and-scold mentality when it comes to identifying vulnerabilities. An approach that's not effective at proactively reducing risk from vulnerable open source software.
The Sonatype Platform already provides comprehensive remediation guidance for developers to select the safest components. It can also quickly identify and replace vulnerable components present in your applications. This latest release of Sonatype Lifecycle makes remediation even easier, while also streamlining workflows to approve components that don't fully conform to policy.
These changes, plus better intelligence for PHP components, help developers identify more vulnerable components faster, saving them time and reducing risk.
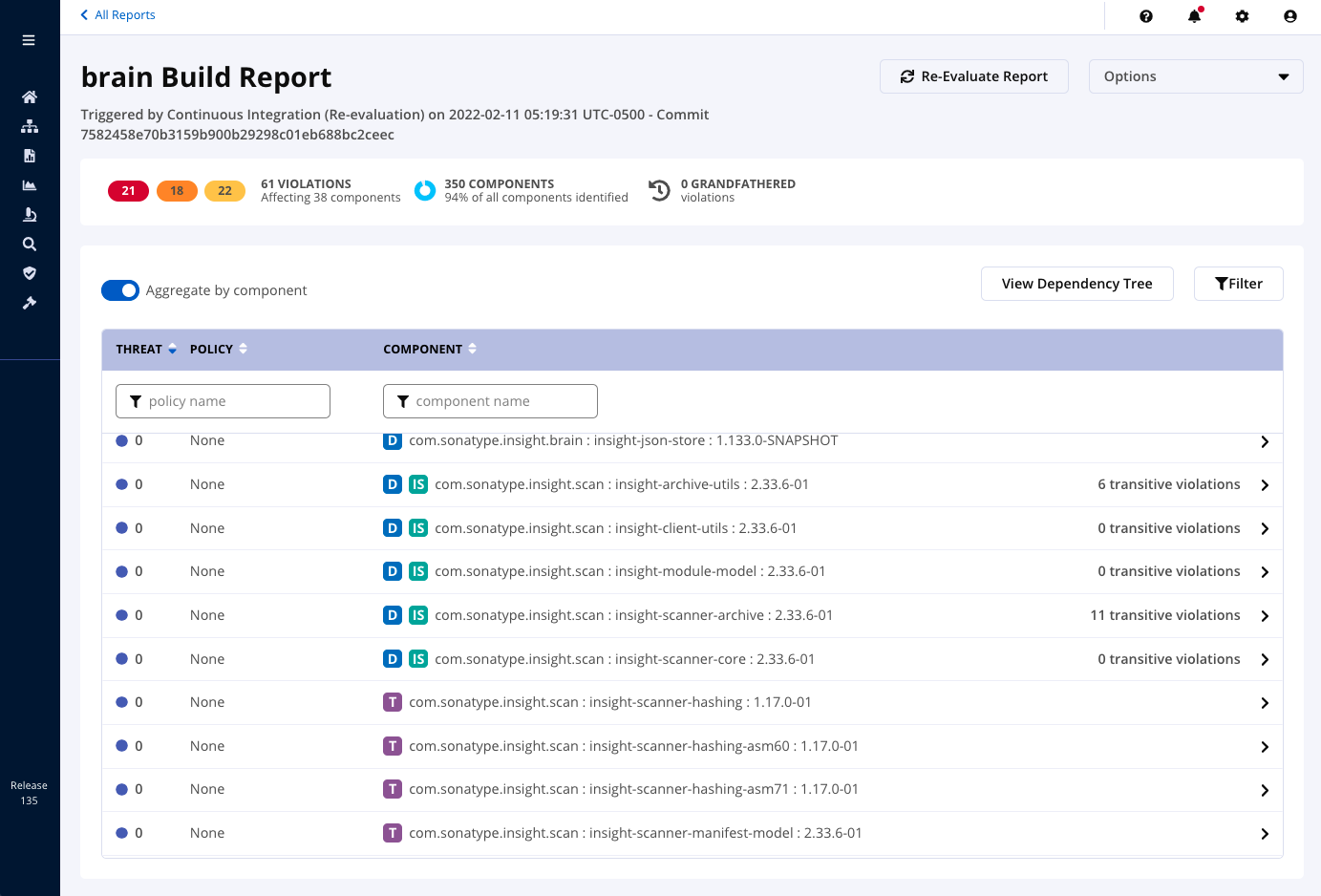
Dependency Tree Visualization
Development teams download direct, open source components every day. By nature of how open source works, these projects are themselves made up of multiple component projects. These are known as "transitive" dependencies, and there can be 100s of them built-in to your software. With each new component, there is a growing risk of unknown components. Are they up to date and secure?
Indications that direct dependencies are free of security issues often aren't assurance that the component projects are safe. Worse, finding and resolving the security risks brought in by these transitive dependencies is a complex and difficult task. Due to the way major projects scale, security and software engineering teams have to spend time figuring out which direct dependency brought a transitive dependency in. Then, once you determine which team owns that problem, it needs to be prioritized.
Especially for larger projects, it can quickly become impossible to efficiently identify and fix these security risks. So how do you resolve all these security risks nested within your component software?
Structural View of Components
Dependency Tree Visualization provides development teams with a new, graphical view that makes identifying and tracing vulnerable libraries easier. The program shows the relationship between direct and transitive dependencies, saving time development teams spend on research and remediation efforts. This means fast prioritization for components upgrading can resolve that.
This view shows component dependencies and their dependencies within an application report using a tree visualization (pictured below).
Zoomed-in view of a the software component dependency structure
The tree view works in combination with existing dependency information from Sonatype Lifecycle. Using dependency type indicators in the Application Analysis Report, users will see attached letters denoting:
D = Direct Dependencies
T = Transitive Dependencies
IS = InnerSource Components
Example of dependency type indicators
This visual analysis makes it easy for developers to quickly locate all intermediate and direct parent components that are utilizing or calling the component within the application. This helps developers identify the best remediation path, usually the direct components to upgrade.
Fix Transitive Issues
The Sonatype Platform now includes the industry's most powerful tool for remediating transitive dependency risk. Sonatype Lifecycle's Transitive Solver shows at a glance how to replace vulnerable components, even when nested deep in components' dependencies, and without causing breaking changes or violating the company's open source policies.

Transitive solver
This policy-driven approach is customizable to your unique business requirements.
The results:
-
Fewer transitive dependency issues entering your projects
-
Reduced resolution time for new transitive vulnerabilities
-
When your team is not constantly putting out fires caused by critical issues, they can start to be proactive, which means productivity and meeting deadlines.
Best of all, developers prefer this less noisy option versus competing tools that run pull requests for every security violation, whether direct or transitive.
Violation Waivers: Get More Details
Quality tools call attention to issues without bullying developers. So while Sonatype Lifecycle flags all components outside company policy, there are cases where these tools can be used without risk. If for example use is limited to internal, temporary, or disconnected from the internet, security, license, or version concerns may not block developers.
Although teams can apply their expertise to find an exception, it's still important to have visibility into those decisions, so developers can have flexibility without ignoring policy. After all, waivers created for unknown software or badly outdated software, for example, can introduce risk into your organization.
Sonatype now makes it easier for teams to manage times when and how a problematic component is allowed. Now, when adding or requesting a waiver, developers can include an expiration date, additional context for reviewers, and comments:

Example waiver screen
Status and ownership are also visible inside Sonatype Lifecycle in the 'Created By' field within the waiver record. Approvers can see who created the specific waiver to raise questions, address comments, or review system policies:

Example waiver with "Created By" view.
If a problem surfaces, teams can quickly determine next steps by understanding the process and decisions behind its use. These controls mean better tracing of responsibility, easier management, and smarter policy – all without boxing in your experts. It also means less risk to your development process when you can easily address questionable open source software components.
AppSec and Development teams will also see less friction caused by waiver requests, saving time and headaches.
Enhanced Data for PHP Components
Teams building PHP applications can now get the most accurate and actionable information available for their open source components. Users downloading packages via Composer will now have higher quality identity data and more complete CVE information, all with fewer false positives and false negatives. Available for both Sonatype Lifecycle and Sonatype Repository Firewall, this means better component insights and vulnerability data in your PHP development.
Request a demo of Sonatype Lifecycle.

Chris is a Product Marketing Manager with Sonatype. Originally from Pittsburgh, PA, Chris studied Communications and Computer Science at the University of Pittsburgh. He enjoys working for Sonatype because of the culture here at the company -- it's diverse and promotes creativity. When he's not ...
Explore All Posts by Chris GoodTags

Try Nexus Repository Free Today
Sonatype Nexus Repository is the world’s most trusted artifact repository manager. Experience the difference and download Community Edition for free.
