In addition to regular vulnerability data research, the Sonatype Security Research Team also contributes to the open source community by going the extra mile when we discover flaws previously not reported. Recall earlier this year when our team discovered they could bypass a fix to the SheetJS project. We took immediate steps to collaborate with the project developers, responsibly disclosing the details of the bypass, and working with them on rolling out a new fix. Consequently, we helped protect our customers by incorporating this newly discovered information into our data.
Fast-forward to recent presentations at DefCon, which highlighted various vulnerabilities… Because DefCon is such a widely recognized event, the Security Research Team revisited the data of vulnerabilities mentioned there, since they were likely to get renewed attention. One such vulnerability we examined was CVE-2019-19507 from "Discovering Hidden Properties to Attack Node.js ecosystem." Like with SheetJS, we discovered that the vulnerability could still be exploited with the existing fix in place.
Json Pattern Validator (JPV) is an open source JSON schema validator, which makes it easy to compare a given JSON object against a schema or particular pattern. A typical use-case for such a package would be to validate that incoming JSON is expected. CVE-2019-19507 allows an attacker to validate objects as arrays, by setting that object’s `constructor.name` to be 'Array.' To fix this problem, JPV was updated to simply check that the constructors matched.
While updating our data for this CVE, Security Researcher Garrett Calpouzos discovered a way to iterate on this attack. By setting the nefarious object's constructor to be `[].constructor`, an attacker could once again successfully masquerade an object as an array and falsely get the JSON data validated by JPV.
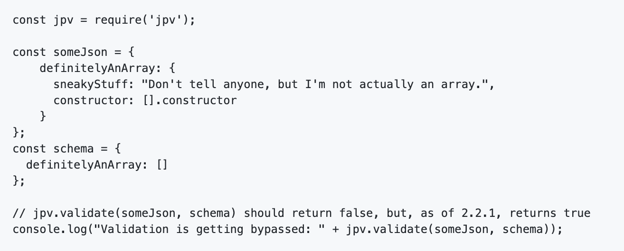
PoC of Attack to Bypass Fix for CVE-2019-19507
Source: GitHub Issue
Upon Calpouzos' discovery, he immediately reached out to the JPV project to report his findings. Working with the project via GitHub Issue #10, he shared a Proof of Concept (PoC) demonstrating how exploitation of the vulnerability was still possible. The project did a commendable job in their response, both in communicating with us and fixing the patched version the very next day after receiving the PoC (two days after our initial communication).
Over the weekend, the project developers added a new section of code to check specifically for arrays, using the native `Array.isArray` function, along with other checks, to ensure that data that claims to be an array is, in fact, an array. This new functionality to account for such an attack has been included in version 2.2.2. Consequently, users of `jpv` should consider upgrading to version 2.2.2 as present in npm.
While a new fix was underway over the weekend, Sonatype customers had already received the updated information on CVE-2019-19507, particularly the following Advisory Deviation:
While researching this vulnerability, the Sonatype Security Research team discovered a bypass for the fix the developer provided for this issue. As of 8/6/2020, we have reported the issue to the developer and are awaiting a response.
To prevent confusion, we have assigned a new vulnerability identifier to this flaw: CVE-2020-17479. Customers using versions of `jpv` containing the fix for CVE-2019-19507 should see this newly assigned identifier in our products (for `jpv` versions <2.2.2).
Cases like these illustrate how interaction with the open source community helps keep components, customers, and their software supply chains secure.
DevOps-native organizations with the ability to continuously deploy software releases have an automation advantage that allows them to stay one step ahead of the hackers. Sonatype customers were notified of the updates pertaining to this vulnerability within hours of the discovery. Their development teams automatically received instructions on how to remediate the risk.
If you're not a Sonatype customer and want to find out if your code is vulnerable, you can use Sonatype's free Sonatype Vulnerability Scanner to quickly find out.
Visit the Sonatype Intelligence Insights page for a deep dive into other vulnerabilities like this one. Or subscribe to automatically receive Sonatype Intelligence Insights hot off the press.

Written by Sonatype Security Research Team
Sonatype's Security Research Team is focused on bringing real-time, in-depth intelligence and actionable information about open source and third party vulnerabilities to Sonatype customers.
Tags
