Protect
Artificial Intelligence predicts known and unknown malware days before any public advisory, protecting you from zero-day attacks.
Control
Tailor remediation policies and assign risk profiles based on your needs
Innovate
Maintain developer velocity while using safe and compliant open-source components.
AI at Sonatype
Sonatype Repository Firewall is the only solution that protects your repository with AI, preventing known and unknown open source risk from entering your software supply chain.
REPOSITORY PROTECTION
Avoid costly supply chain attacks
Identify intentionally malicious packages
Let AI behavioral analysis tell you what’s suspicious
Improve compliance
Boost the DevSecOps experience
Debunking the Myth of Security vs. Productivity
A staggering 29% of popular projects contain vulnerabilities. Outsmart risk with Sonatype’s open source security software.
“The Sonatype Platform is consistent with our gradual rise in maturity. The product brings richness from the very first use. Whether you're a beginner or a Sonatype expert, it gives you the ability to find the solutions you need. All our teams are delighted to be able to use it.”
POLICY COMPLIANCE
Automate your policy enforcement
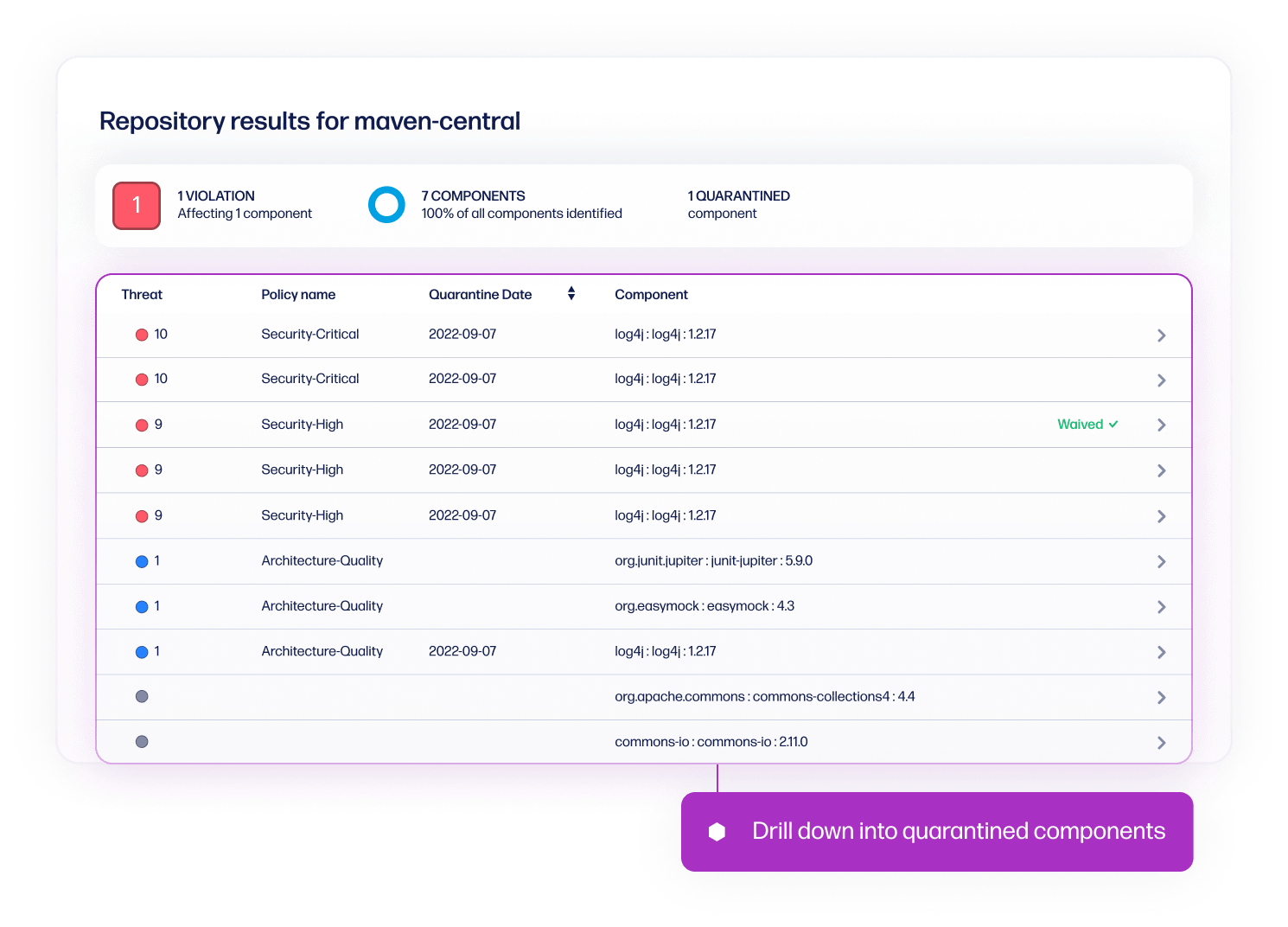
Set policy based on risk tolerance
Protect against the unknown
Configure automatic compliance
A better way to do open source security
Ensure your team is working with the best available open source. Sonatype Repository Firewall sits at the front of your artifact repository to defend your software supply chain. Combining Artificial Intelligence (AI) behavioral analysis and automated policy enforcement, easily intercept intentionally malicious packages and enforce policies to improve security and compliance.

Run products anywhere
Cloud
Self Hosted
Air-Gapped
Explore the Sonatype platform
![]()
Intercept malicious open source at the door.
You are here
Work with the tools you already use
Universal repository support

Sonatype Nexus Repository Pro
Better together: Protect your Sonatype Nexus Repository (Pro) with Firewall.
JFrog Artifactory
Using Artifactory? No problem.Sonatype Repository Firewall supports JFrog’s Artifactory.
Firewall language support
 C
C
 C++
C++
 Go
Go
 Gosu
Gosu
 Java
Java
 PHP
PHP
 Python
Python
 R
R
 Ruby
Ruby
 Scala
Scala
 Swift
Swift
 Visual Basic
Visual Basic
Firewall package support
 Maven
Maven
 npm
npm
 PyPi
PyPi
 Nuget
Nuget
 Yum
Yum
 Go
Go
 Rubygems
Rubygems
 Conan
Conan
 Cargo
Cargo
 Gradle
Gradle
 Conda
Conda
 R
R
Enterprise protection from attacks
Features

-
Protection from unknown vulnerabilitiesYes for npm, PyPl
-
Hosted repository protection from namespace confusion attack
-
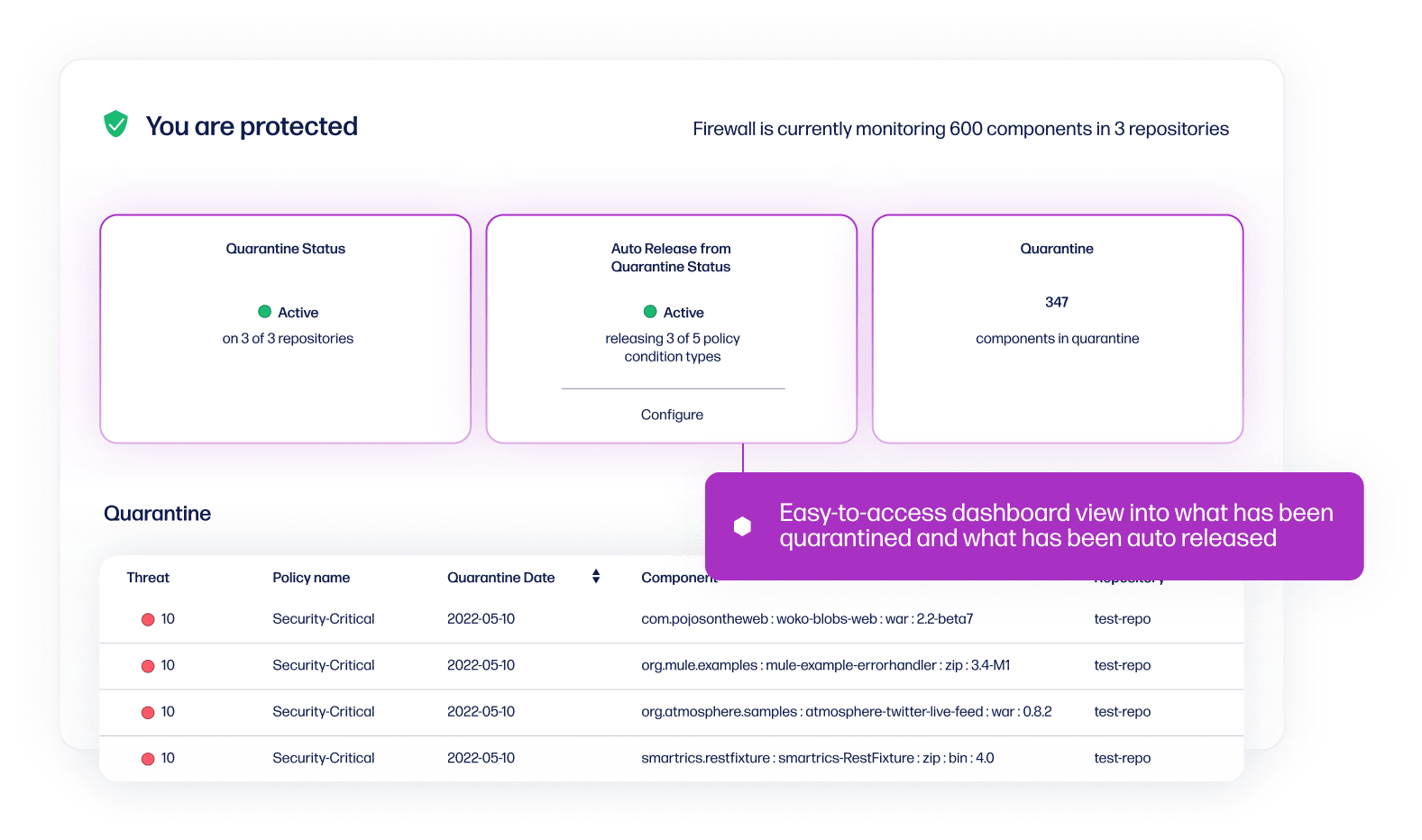
Suspicious auto-quarantine
-
Automatic release from quarantine
-
Automated version replacement for dependencies
-
New reports and views for application security and developers
-
Improved developer experience
-
Support for artifactory enterprise
