Securing software development with Sonatype Air-Gapped Environment (SAGE)
By Wade Peckman
4 minute read time

Developers everywhere build modern applications from reusable pieces of code downloaded from repositories such as Maven Central.
However, consider a government agency developing a software application for analyzing classified data or supporting operational missions. If someone outside the agency gains knowledge about the specific components being used, they could discern the nature of the application.
Unauthorized people gaining understanding of utilized open source components not only exposes the agency's ongoing projects but also creates an opportunity for a malicious actor to introduce harmful code. This code could disrupt the software's functions, jeopardize the agency’s operations, and lead to severe mission impacts.
This scenario underscores the critical importance of protecting sensitive information and highlights why using the Sonatype Air-Gapped Environment (SAGE) is essential to enhancing security and mitigating potential threats.
The need for air-gapped solutions for secure software development
Traditionally, a team of software developers in a government agency might decide to put their faith in a "golden repository" that restricts usage to only those components approved by their security, licensing, and architecture teams. Unfortunately, this approach limits innovation and doesn’t consider newly discovered vulnerabilities.
Employing a software composition analysis (SCA) tool such as Sonatype Lifecycle and using a software bill of materials (SBOM) for component monitoring and governance is a better way. This allows teams to pinpoint the location of vulnerable components and determine where remediation needs to take place. Case in point: Equifax's massive 2017 breach occurred in part because they failed to locate the Struts 2 vulnerability in their environment.
Why choose Sonatype Air-Gapped Environment (SAGE)?
As cybersecurity accelerates in priority for public sector organizations, the need to create secure environments becomes even more critical.
SAGE is an innovative solution for teams wanting to operate in disconnected DevSecOps environments. For agencies and organizations dealing with highly classified and sensitive information, SAGE provides an additional layer of security by minimizing the threat surface and reducing the risk of vulnerabilities being exploited by bad actors, both from inside and outside the organization.
When organizations cannot support their software development efforts in disconnected environments, they risk opening them up to internal or external exploits. With SAGE, organizations can identify what vulnerabilities are in their software without anyone knowing what components are in their applications.
How does SAGE work?
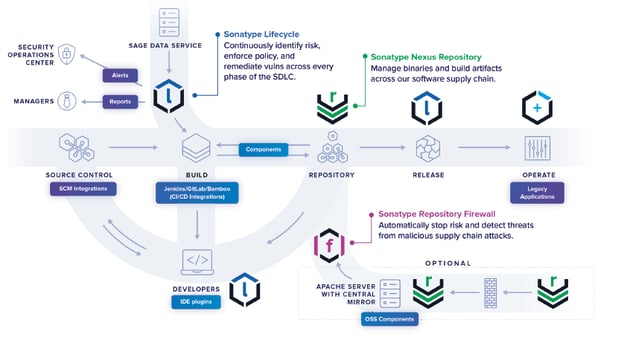
At its core, SAGE is designed to help secure your software development environment. It accomplishes this by encapsulating the data service that we provide for our connected on-premises and SAAS customers and providing daily incremental updates of our high-quality vulnerability information on open source components. For ease of deployment, we provide rpms, Dockerfiles, and Helm charts for all of the SAGE software components (Sonatype Lifecycle, Sonatype Nexus Repository, and Sonatype Data Service). Using Helm charts to deploy into a Kubernetes environment results in a highly scalable system of systems capable of supporting thousands of developers.
Daily incremental updates of our world-class vulnerability information mean SAGE can support the advanced features of Sonatype Repository Firewall. For example, new releases of a software package can create high risk. The new release can contain an undiscovered security vulnerability, a new license, or malware. Sonatype Repository Firewall's protection from "Pending" and "Suspicious" components is designed to protect your software supply chain from potentially dangerous new releases — including unicode trojans, typosquatting, and more.
What are the benefits of using SAGE?
In an age where data security is non-negotiable, organizations need solutions that can effectively shield their software development environments.
In this context, SAGE offers a range of compelling benefits:
- Minimize the threat surface. Having an air-gapped environment is the equivalent of a “digital moat” that minimizes the attack surface, isolating the organization from malicious actors.
- Mitigate insider threat. SAGE enables teams to identify and block vulnerable components, allowing them to confidently choose safer components that reduce exploits, while also preventing insider threats posed by bad actors.
- Protect sensitive information. Through automated policy enforcement, SAGE accelerates the deployment of secure applications while ensuring the protection of sensitive information and continuous monitoring.
Empowering secure software development with SAGE
The software application development landscape continues to shift in the face of constantly evolving challenges and opportunities. For most organizations, the ability to deliver robust software by securing their development environments is a critical business imperative and for government agencies, it is essential for protecting national security.
SAGE empowers application development and portability in air-gapped environments, offering a critical layer of protection for sensitive data. By facilitating software development in disconnected environments, SAGE provides a critical layer of defense against both insider threats and external vulnerabilities.
Discover how Sonatype's air-gapped solution can fortify your software supply chain against external and internal threats. Reach out to us for a comprehensive understanding of how SAGE can transform your software development security posture.
-Mar-07-2024-09-28-41-3856-PM.png?width=50&name=image%20(1)-Mar-07-2024-09-28-41-3856-PM.png)
Written by Wade Peckman
Wade is the Vice President, Public Sector Customer Success at Sonatype.
Read Bio