Software Supply Chain Maturity
Software supply chain maturity - peer insights
In this year's report, we dive into insights gleaned from 621 enterprise engineering professionals, providing invaluable perspectives on software supply chain management and organizational development practices. Our analysis draws from a comprehensive survey that explored the multifaceted landscape of software supply chain management, including the utilization of open source software (OSS) components, dependency management, governance, approval processes, and tooling. The survey also covered questions related to development practices, demographics, and job satisfaction levels, culminating in a more holistic view of software supply chain maturity at an enterprise and industry level.
Expanding horizons
Over the last decade, the software supply chain landscape has experienced rapid and significant changes. In the past year alone, the emergence of generative AI capabilities and introduction of global regulatory initiatives spurred modernization efforts in software development across industries.
To further understand this ever-evolving landscape, we marry last year’s findings with what’s changed today. We explore interesting year-over-year (YoY) trends, examine the growing demand for software bills of materials (SBOMs), and identify key practices aimed at not wasting developer time. Furthermore, we take a deeper look at companies affected by open source risk, particularly those who have experienced security breaches. Through this investigation, we aim to shed light on how these organizations may differ from their peers and provide insights into bolstering security measures within the software supply chain.
Continuing objectives and methodologies
Consistent with our approach in previous editions, this chapter maintains two core objectives:- Provide a benchmark and maturity model that enables organizations to assess their practices in comparison to their industry peers.
- Determine if reported software supply chain practices align with desirable outcomes.
Eight themes of mature software supply chain management practices

 REMEDIATION
REMEDIATION
How do you implement fixes to address identified OSS component risk?

 SUPPLIER HYGIENE
SUPPLIER HYGIENE
Do you know if your OSS components come from a trusted, quality supplier?
 APPLICATION INVENTORY
APPLICATION INVENTORY
Do you know the key details of your organization's applications, such as stakeholders, ownership, construction, and the software bill of materials (SBOM) for OSS components?
 GIVING BACK
GIVING BACK
Do you contribute to the OSS community?
 POLICY CONTROL
POLICY CONTROL
What is your tolerance for risk? Do you have automated policy enforcement?
 PROJECT CONSUMPTION
PROJECT CONSUMPTION
Do you govern OSS component selection?
 BUILD & RELEASE
BUILD & RELEASE
Do you understand how your software "parts" and processes come together to build and release applications into production?
 DIGITAL TRANSFORMATION
DIGITAL TRANSFORMATION
What plans, resources, and training do you have to help institutionalize new processes and tools?
How mature are today’s software supply chains?
We've distilled and presented collective insights from the 621 surveyed individuals in Figure 4.1. To develop this summary, we averaged each individual’s responses on questions that align with the eight themes. In each theme, we scored the responses from 1 to 5, corresponding to the five stages of software supply chain maturity. From Unmanaged (least mature) to Monitor & Measure (most mature), as noted in Figure 4.2.
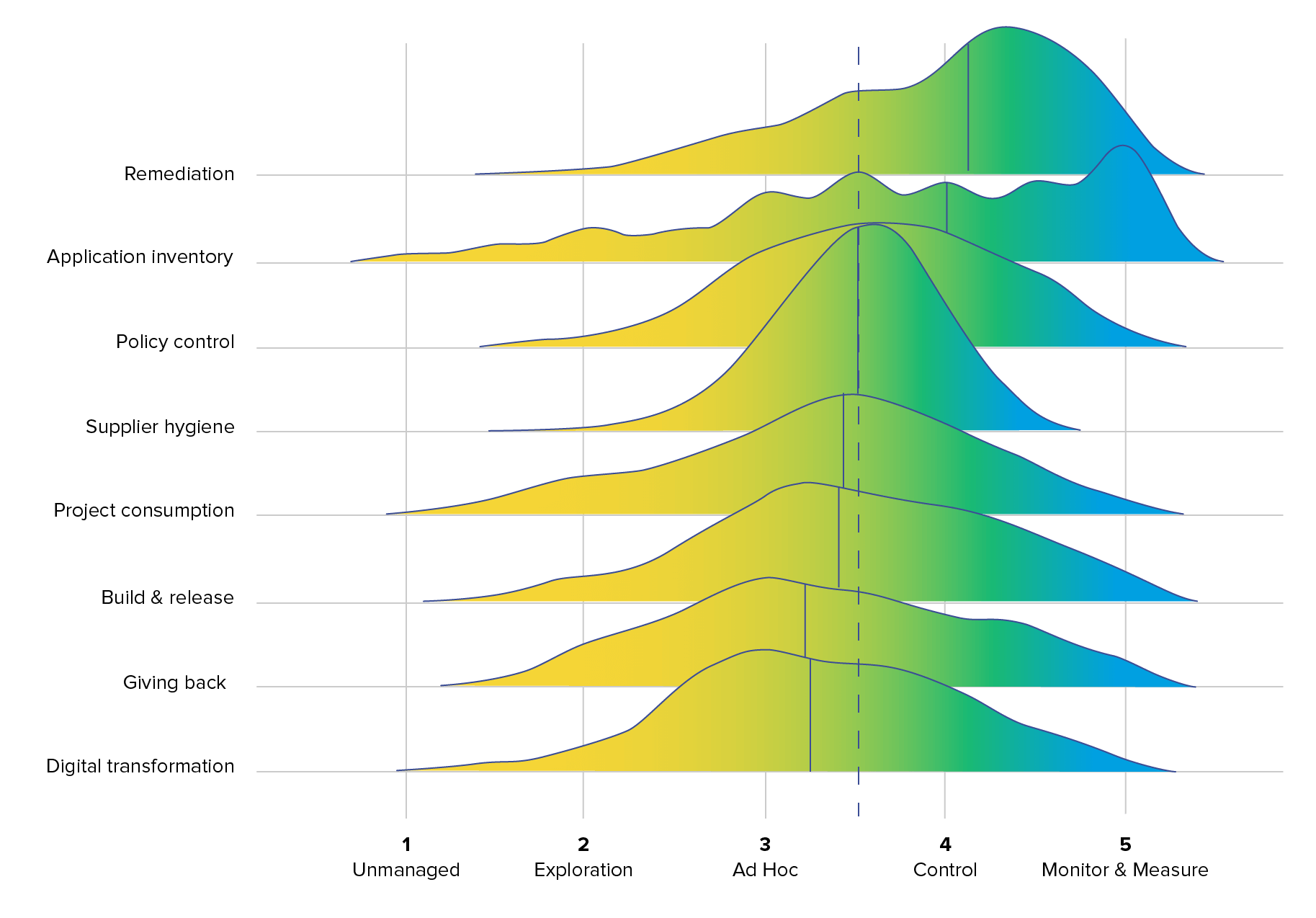
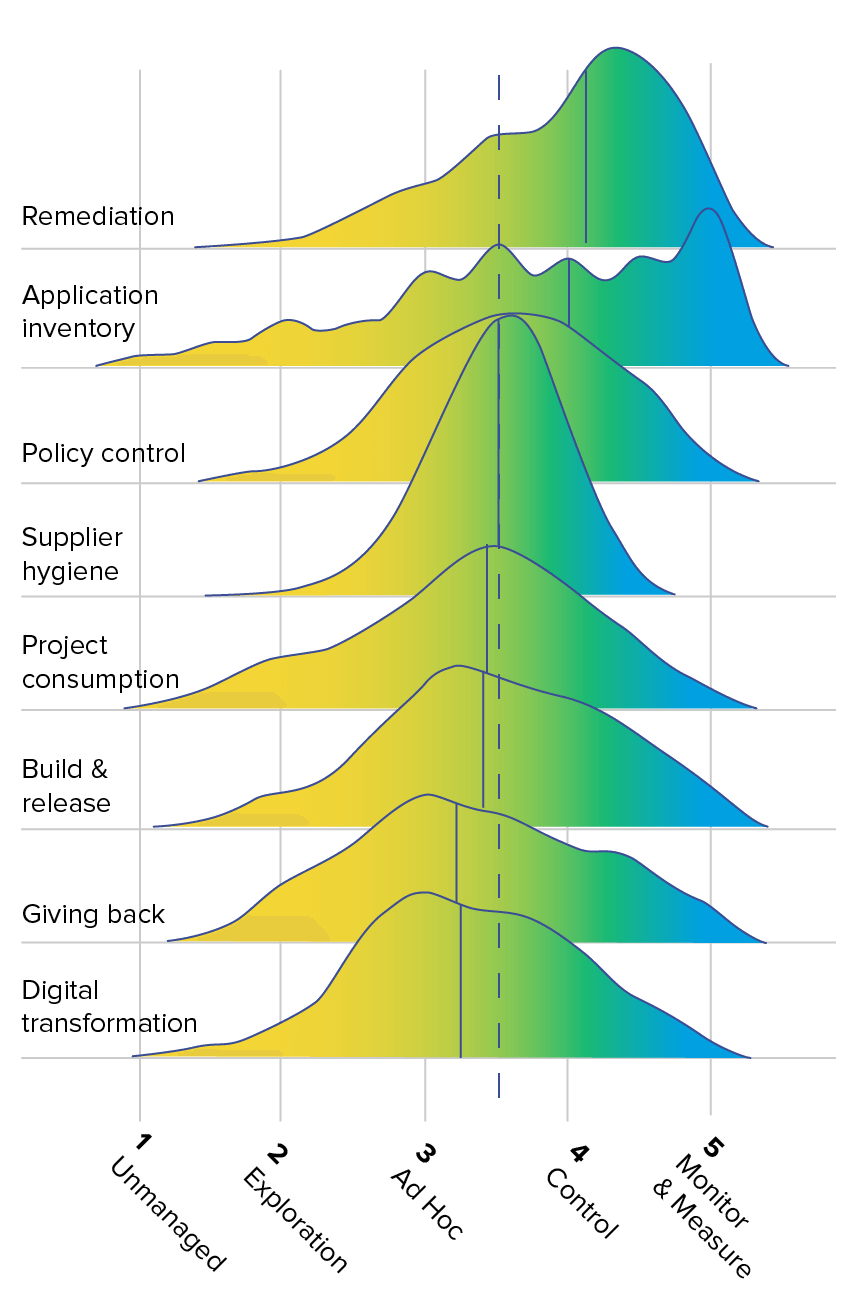
FIGURE 4.2. FIVE STAGES OF SOFTWARE SUPPLY CHAIN MANAGEMENT MATURITY
Perception is disconnected from reality – again
In last year’s survey, the data showed a notable pattern: respondents tended to self-report a higher level of software supply chain maturity than their actual stage of advancement, leaving many with an inflated sense of security. This trend persists into this year’s findings.
Overall, this year’s survey reveals that respondents generally demonstrated lower levels of maturity in the Digital Transformation theme and higher levels of maturity in Remediation. This consistent year-over-year trend underscores a fascinating disparity between how survey respondents self-assess their progress in actively addressing vulnerabilities (indicative of higher maturity) versus their capacity to garner essential buy-in, sponsorship, training, and operational processes for effective remediation (reflecting lower maturity).
From this, a striking statistic emerges: 67% of respondents feel confident that their applications do not rely on known vulnerable libraries. However, nearly 10% of respondents reported that their organizations had security breaches due to open source vulnerabilities in the last 12 months, while 20% were unsure if their organization had been breached. Pair this with the objective information we saw in Chapter 1 – that 1 in 8 open source downloads have a known vulnerability – and it’s clear that no matter how we look at it, there continues to be a software supply chain management problem.
To get a sense of how your organization compares, take this short quiz on software supply chain maturity.
How mature is your software supply chain? Take the quiz.
How have software supply chain management trends changed?
The software supply chain plays a vital role in modern development processes. Understanding its dynamics is crucial for mitigating risk and ensuring operational efficiency. This section unveils key insights from our survey of engineering professionals, offering a comparative analysis of this year’s responses to those of the previous year. By analyzing these year-over-year trends, we gain a clear view of significant changes and evolutions in the landscape of the software supply chain.
Finding #1: Increased focus on open source risk
In a landscape marked by the growing volume of open source, efficiency in software development is the key to not wasting developer time. This year, our survey results highlighted the interplay between effective tools, developer satisfaction, and optimized work processes. Respondents reported an increase in the use of integrated tooling (+9.8%), growing awareness of and focus on open source risk (+9.3%), improved dependency upgrade decisions (+9.6%), and greater comfortability in software supply chain management (+77%) - all of which point to a maturing market and an increasing industry-wide understanding of the downstream threats vulnerable open source poses.
Changes in supply chain management trends
ADOPTION OF INTEGRATED TOOLING
One notable trend observed this year is a decline in the reliance on ad-hoc reports for obtaining risk information about open source libraries. A substantial decrease of 14.5% was recorded among respondents who received reports from external sources. However, a corresponding 9.8% increase was found in the integration of risk information into continuous integration (CI) and build processes. This shift aligns with the changing preferences, where more professionals now favor obtaining risk information within their existing workflows, rather than relying on separate reports.
GROWING FOCUS ON OPEN SOURCE RISK
Another interesting finding: open source is very much a focus for engineering teams, and is a growing one at that. There was a significant increase in respondents disagreeing with the statement that "open source risk is not currently a focus" for their organization (9.3%), and likewise, a decrease in those agreeing (-9.6%).
IMPROVED UPGRADE DECISIONS
Respondents reported a decreasing number of times that dependency upgrades "always/often/frequently" broke the functionality of their application, and an increase in the number of times dependency upgrades rarely or never broke their application's functionality. Not only does this point to respondents getting better at handling dependency upgrades and avoiding breaking changes, it also shows a deeper understanding of open source hygiene.
GREATER COMFORT EQUALS GREATER EFFICIENCY
Overall, respondents felt more comfortable and familiar with topics surrounding software supply chain management this year. There was a 7.7% increase in those that kept up with software supply chain trends.
In summary, although there is an increased focus on and awareness of open source risk, organizations have ample ground to cover in implementing best practices for mitigating these risks effectively.
Organizations continue to grapple with immature practices that waste time and resources – weighing teams down and slowing development.
Finding #2: Rise in demand for software bills of materials
Thanks to mandates outlined in President Biden's Executive Order 14028, Improving the Nation’s Cybersecurity and growing global regulatory efforts, one open source best practice that is experiencing a growth in adoption is the use of an SBOM.An SBOM serves as a comprehensive inventory, outlining the various components and dependencies of a software application. It provides a detailed list of the software's building blocks, including open source and third-party libraries, along with their respective versions. This document serves as a critical resource for understanding and managing the software supply chain. By enabling developers and organizations to accurately track and assess the security and licensing aspects of software components, SBOMs play a vital role in software development, cybersecurity, and regulatory compliance. SBOMs provide transparency and visibility into software composition, thereby facilitating efficient risk management, enhancing vulnerability response, and supporting effective software maintenance. Ultimately, while the creation of SBOMs themselves doesn’t equate to security, the adoption of SBOMs contributes to building secure, reliable, and trustworthy software systems, benefitting both software producers and consumers.
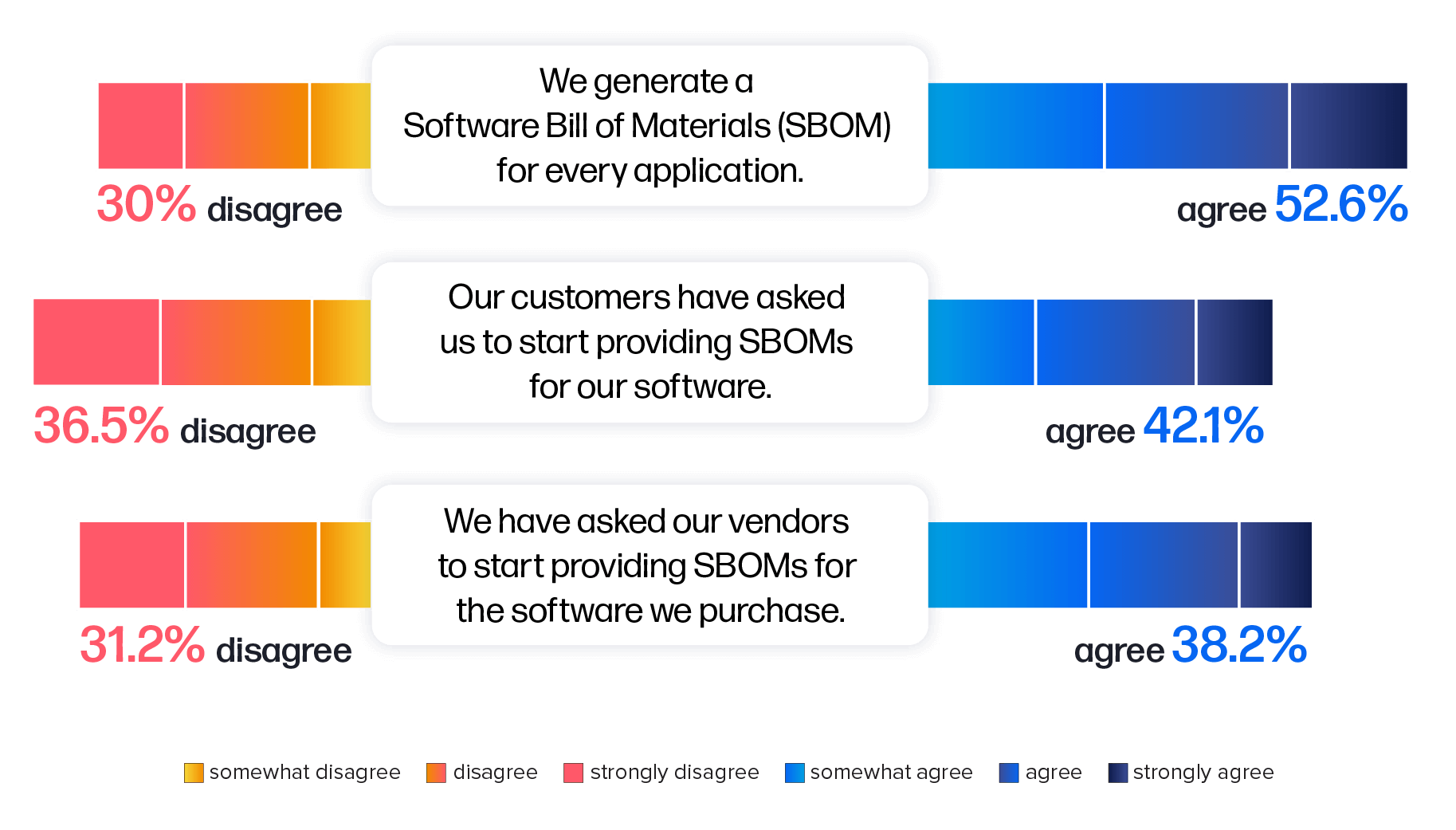
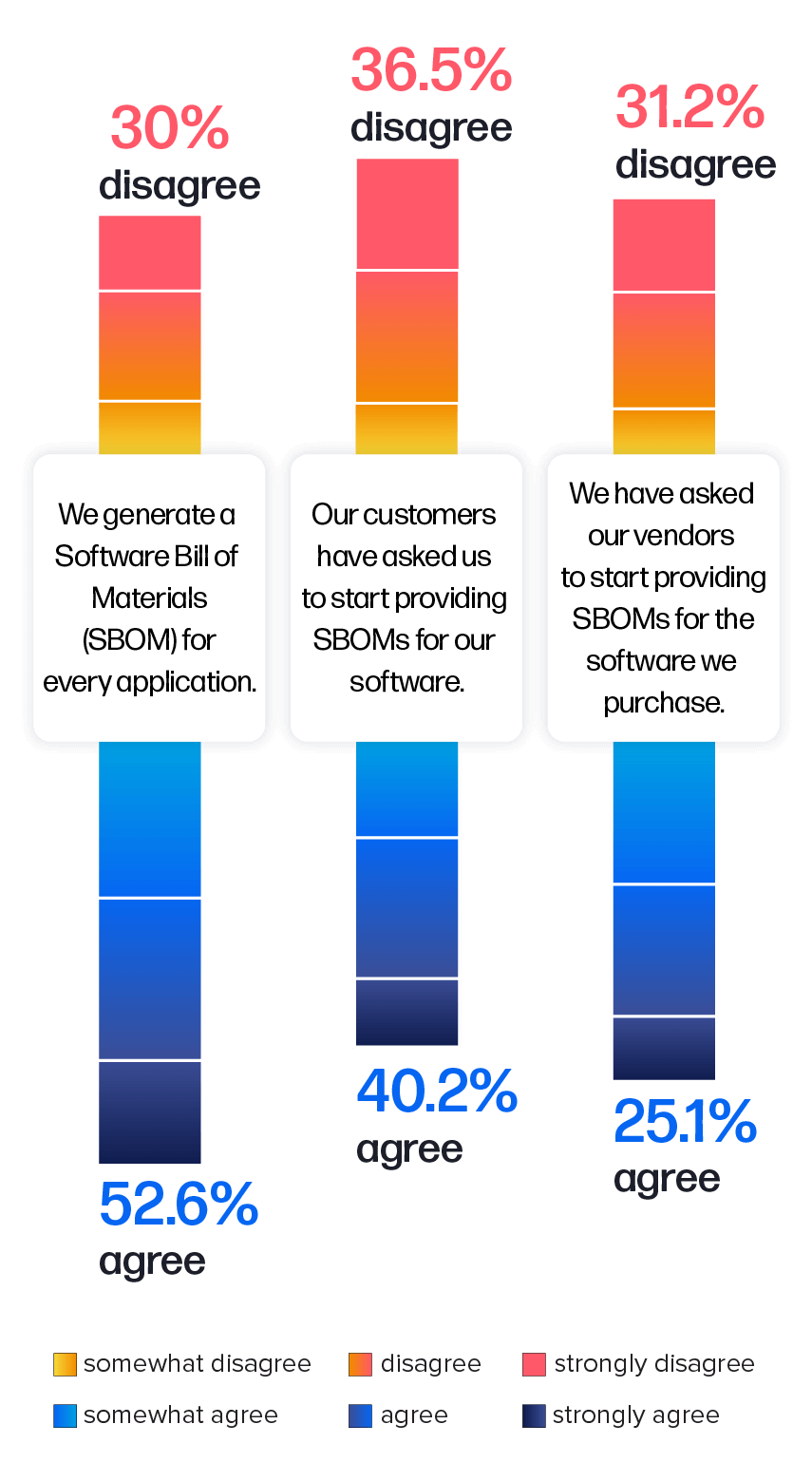
This year, we took a deeper look at the usage and demand for SBOMs. Findings revealed that nearly 53% of the surveyed engineering professionals reported they are generating an SBOM for every application (Figure 4.3). Notably, respondents who adopted this practice were less likely to report security breaches.
In addition, nearly half of the respondents have started asking vendors to supply SBOMs for purchased software, underscoring a higher demand for increased transparency in software supply chains.
Finding #3: The critical connection of hygiene and speed in risk mitigation
This year, we investigated how organizations have been impacted by open source risk, particularly those that have experienced security breaches.Our analysis revealed a connection between security breaches and suboptimal management practices such as:
- deploying every change directly to production;
- breaking the functionality of their applications with dependency upgrades; and
- adhering to an entirely waterfall development practice.
Overall, our survey revealed that only 22% of organizations become aware of new open source vulnerabilities within a day of disclosure. Thirty-nine percent (39%) discover them within one to seven days, and 28% take over a week to become aware.
FIGURE 4.4. TIME TO REMEDIATE KNOWN VULNERABILITIES AFTER DETECTION
1 week and never
For organizations navigating the complexities of open source risk and striving for swift mitigation, the path to software supply chain maturity emerges as a pivotal strategy. This enables them to enhance their resilience, ultimately fortifying their security posture and safeguarding against potential breaches.
These findings align with the eight themes of software supply chain management outlined at the beginning of this section. These themes encompass practical strategies aimed at not only enhancing security but also at optimizing developer productivity and reducing the waste of developer time. The journey toward software supply chain maturity is not just a path to enhanced security — it’s also a path to stop wasting developer time. By improving software supply chain maturity, organizations create an environment in which developers can focus on innovation, leading to more resilient and secure software.
The journey toward software supply chain maturity is not just a path to enhanced security — it’s also a path to stop wasting developer time. By improving software supply chain maturity, organizations create an environment in which developers can focus on innovation, leading to more resilient and secure software.
Establishment and Expansion of Software Supply Chain Regulations and Standards

