Sonatype auditor
Examine open source components within your third party or legacy production apps.
FULL VISIBILITY
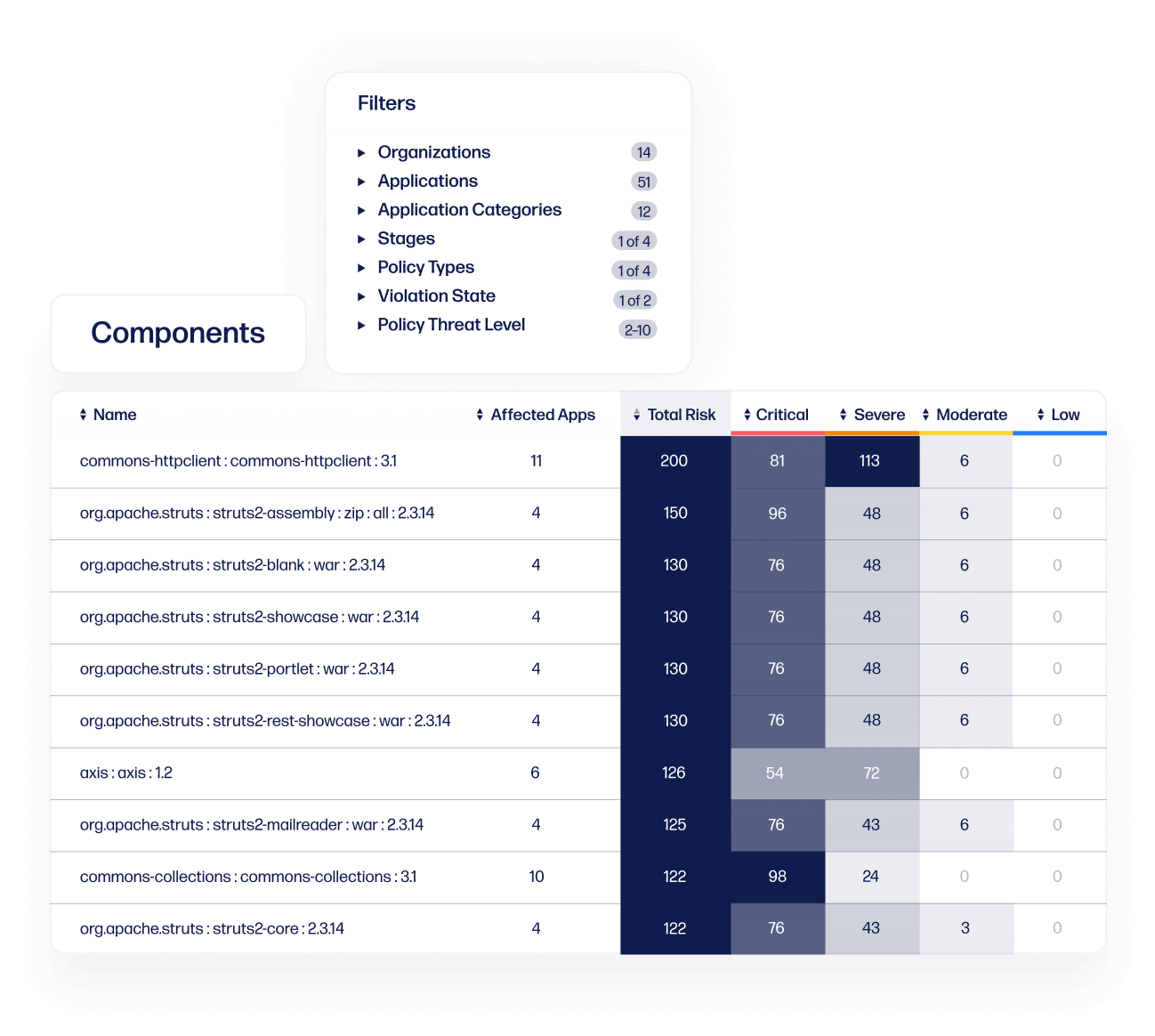
Generate a software bill of materials
Automatically generate a software bill of materials to identify open source components used within your third-party or legacy applications. Then easily identify components that violate your open source policies.
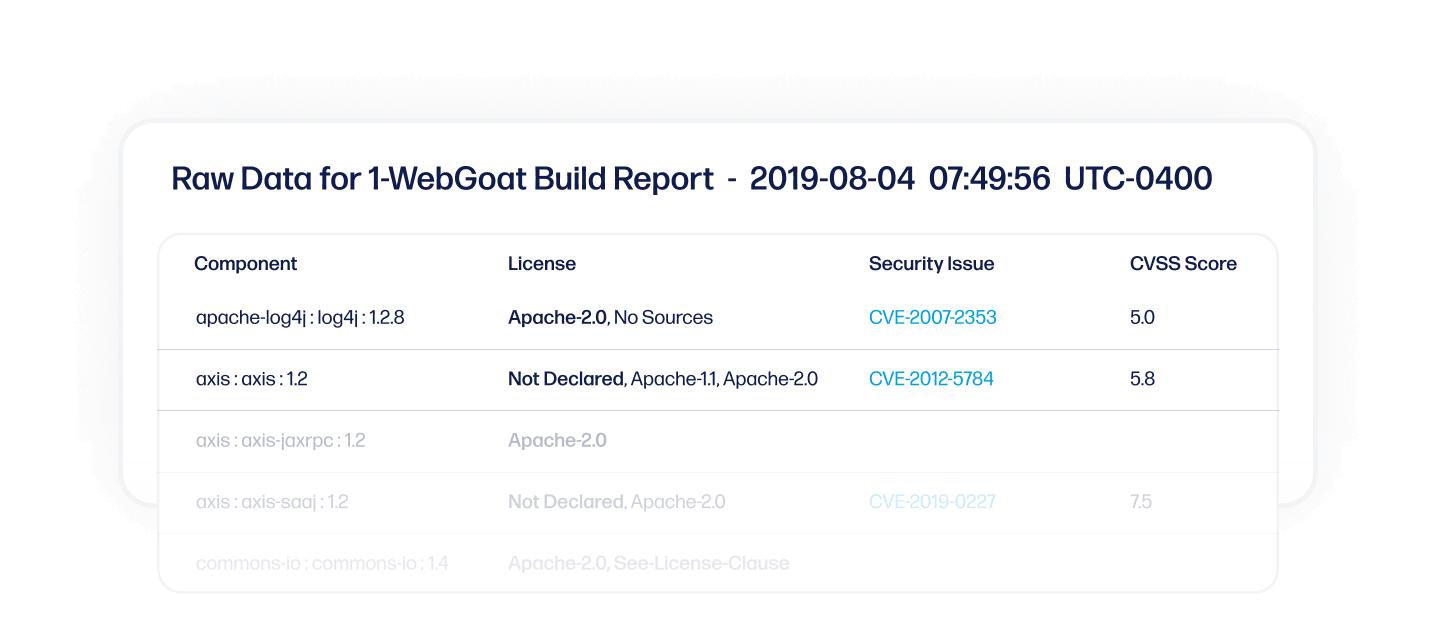
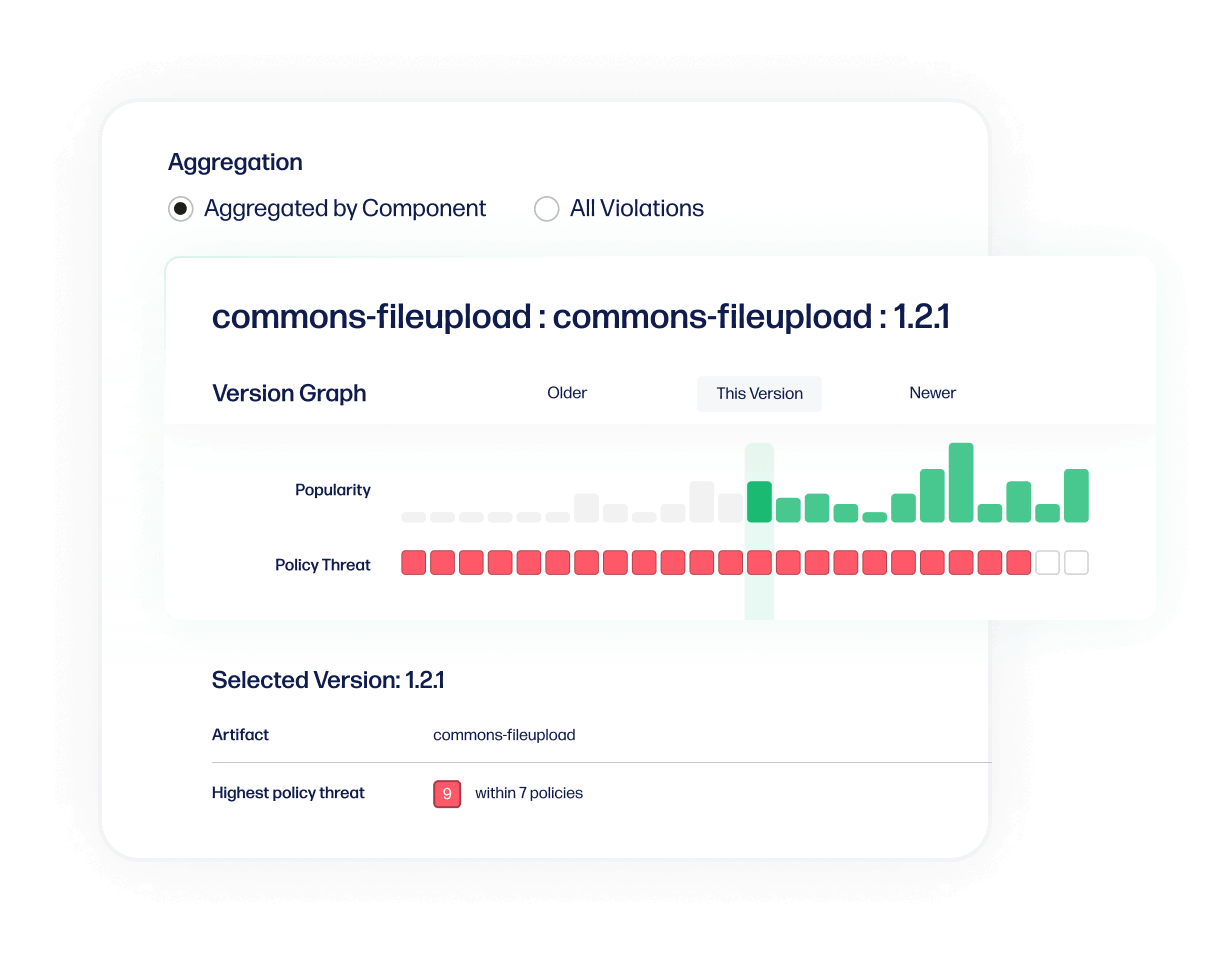
RISK ANALYSIS
Analyze third party security risks
Scan third party applications before accepting them to clearly see if any restricted licenses or security vulnerabilities exist. Then access remediation guidance to fix any issues as quickly as possible.
REAL-TIME ALERTS
Monitor your apps in production
Keep your open source components free of security vulnerabilities with continuous monitoring. Know the minute a newly disclosed vulnerability is found so you can take immediate action and eliminate any threats to your organization.
Secure earlier in your SDLC with Lifecycle
| Features |
|
|
|---|---|---|
| Customized policy | yes | yes |
| Automatically generates a software bill of materials | yes | yes |
| Remediation guidance Waivers, license overrides |
yes | yes |
| Continuous monitoring | yes | yes |
| Integrates with CI/CD | no | yes |
| Integration to the IDE | no | yes |
| Automatic enforcement Fail builds, creates JIRA tickets, emails |
no | yes |
| Features | |
|---|---|
| Customized policy | yes |
| Automatically generates a software bill of materials | yes |
| Remediation guidance Waivers, license overrides |
yes |
| Continuous monitoring | yes |
| Integrates with CI/CD | no |
| Integration to the IDE | no |
| Automatic enforcement Fail builds, creates JIRA tickets, emails |
no |
| Features | |
|---|---|
| Customized policy | yes |
| Automatically generates a software bill of materials | yes |
| Remediation guidance Waivers, license overrides |
yes |
| Continuous monitoring | yes |
| Integrates with CI/CD | yes |
| Integration to the IDE | yes |
| Automatic enforcement Fail builds, creates JIRA tickets, emails |
yes |
Explore the Sonatype platform.
Build fast with centralized components.
Intercept malicious open source at the door.
Reduce risk across software development.
Simplify SBOM compliance and monitoring.